redo Jump to...
print Print...
(from BBC News) — Hackers used internet-connected home devices, such as CCTV cameras and printers, to attack popular websites on Friday, security analysts say.
Twitter, Spotify, Netflix and Reddit were among the sites taken offline on Friday.
Each uses a company called Dyn, which was the target of the attack, to direct users to its website.
Security analysts now believe the attack used the “internet of things” – web-connected home devices – to launch the assault.
Dyn is a DNS service – an internet “phone book” which directs users to the internet address where the website is stored. Such services are a crucial part of web infrastructure.
On Friday, it came under attack – a distributed denial of service (DDoS) – which relies on [millions] of machines sending co-ordinated messages to overwhelm the service.
The “global event” involved “tens of millions” of internet addresses.
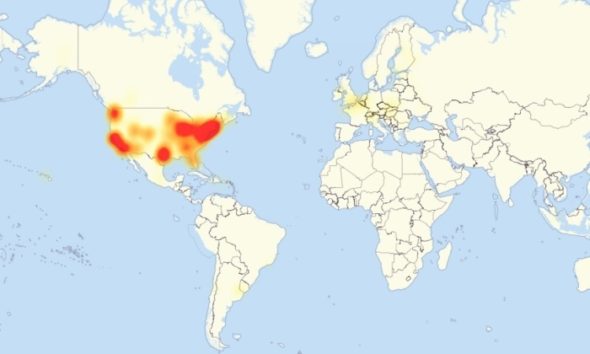
A map of Friday’s massive DDOS attack and the internet outages involved. (Image: PC World/Downdetector)
Security firm Flashpoint said it had confirmed that the attack used “botnets” infected with the “Mirai” malware.
Many of the devices involved come from Chinese manufacturers, with easy-to-guess usernames and passwords that cannot be changed by the user – a vulnerability which the malware exploits.
“Mirai scours the Web for IoT (Internet of Things) devices protected by little more than factory-default usernames and passwords,” explained cybersecurity expert Brian Krebs, “and then enlists the devices in attacks that hurl junk traffic at an online target until it can no longer accommodate legitimate visitors or users.”
The owner of the device would generally have no way of knowing that it had been compromised to use in an attack, he wrote.
Mr. Krebs is intimately familiar with this type of incident, after his website was targeted by a similar assault in September, in one of the biggest web attacks ever seen.
It has emerged that the BBC’s website was also briefly caught up in Friday’s attack. The BBC is not a customer of Dyn itself, but it does use third-party services that rely on the domain name system hosting facilities provided by Dyn.
I understand that these include Amazon Web Services – the retail giant’s cloud computing division – and Fastly – a San Francisco-based firm that helps optimise page download times.
Both companies have acknowledged being disrupted by the DDoS assault. Only some BBC users, in certain locations, would have experienced problems and they did not last long.
But there are reports that other leading media providers also experienced similar disruption.
It serves as a reminder that despite the internet being a hugely robust communications system, there are still some pinch points that mean a targeted attack can cause widespread damage.
The incidents mark a change in tactics for online attackers.
DDoS attacks are typically aimed at a single website. Friday’s attack on Dyn, which acts as a directory service for huge numbers of firms, affected several of the world’s most popular websites at once.
The use of internet-connected home devices to send the attacking messages is also a relatively new phenomenon, but may become more common.
The Mirai software used in these attacks was released publicly in September – which means anyone with the skill could build their own attacking botnet.
On social media, many researchers and analysts expressed frustration with the security gap being exploited by attackers.
“Today we answered the question ‘what would happen if we connected a vast number of cheap, crummy embedded devices to broadband networks?'” wrote Matthew Green, an assistant professor at the Johns Hopkins Information Security Institute.
Jeff Jarmoc, head of security for global business service Salesforce, pointed out that internet infrastructure is supposed to be more robust.
“In a relatively short time we’ve taken a system built to resist destruction by nuclear weapons and made it vulnerable to toasters,” he tweeted.
Reprinted here for educational purposes only. May not be reproduced on other websites without permission from BBC News.
Questions
1. The first paragraph of a news article should answer the questions who, what, where and when. List the who, what, where and when of this news item. (See paragraph 2 for more details) (NOTE: The remainder of a news article provides details on the why and/or how.)
2. Name some of the popular websites were affected by the attack on Friday.
3. Define the following as used in the article:
a) internet of things (para. 4)
b) DNS service (para. 5)
c) DDoS (para. 6)
d) botnet (para. 8)
e) malware (para. 8)
4. a) Explain how the hackers were able to use internet-connected home devices in their attack.
b) List several types of internet-connected home devices that were used by the hackers in this attack.
5. How is this attack different from previous online attacks?
6. What, if any, immediate action do you think the following should take:
- Dyn Company (and others like it)
- the affected websites (including Twitter and Spotify)
- the companies that sell the internet connected home devices that were used in the attack (those manufactured in China)
- the Obama administration, (the U.S. State Department, Department of Homeland Security, Department of Defense…)
- the people who own internet connected devices made in China
Background
FURTHER INFORMATION: Chinese firm admits its hacked products were behind Friday’s massive DDoS attack
(PC World, Sunday, Oct 23, 2016) – A Chinese electronics component manufacturer says its products inadvertently played a role in a massive cyberattack that disrupted major internet sites in the U.S. on Friday.
Hangzhou Xiongmai Technology, a vendor behind DVRs and internet-connected cameras, said on Sunday that security vulnerabilities involving weak default passwords in its products were partly to blame.
According to security researchers, malware known as Mirai has been taking advantage of these vulnerabilities by infecting the devices and using them to launch huge distributed denial-of service attacks, including Friday’s outage.
“Mirai is a huge disaster for the Internet of Things,” Xiongmai said in an email to IDG News Service. “(We) have to admit that our products also suffered from hacker’s break-in and illegal use.”
Mirai works by enslaving IoT (Internet of Things) devices to form a massive connected network. The devices are then used to deluge websites with requests, overloading the sites and effectively taking them offline.
Because these devices have weak default passwords and are easy to infect, Mirai has been found spreading to at least 500,000 devices, according to internet backbone provider Level 3 Communications.
Xiongmai says it patched the flaws with its products in September 2015 and its devices now ask the customer to change the default password when used for the first time. But products running older versions of the firmware are still vulnerable.
To stop the Mirai malware, Xiongmai is advising that customers update their product’s firmware and change the default username and passwords to them. Customers can also disconnect the products from the internet.
Botnets created from the Mirai malware were at least partly responsible for Friday’s massive internet disruption, according to Dyn, the DNS service provider targeted in the assault.
“We observed 10s of millions of discrete IP addresses associated with the Mirai botnet that were part of the attack,” Dyn said in statement.
The DDOS attack, which flooded sites with an overwhelming amount of internet traffic, slowed and stopped access to Twiiter, Spotify, PayPal and many more services.
Although Dyn managed to fend off the disruption and restore access to its service, Mirai-powered botnets could easily strike again. Earlier this month, the unknown developer of the Mirai malware released its source code to the hacker community. Security firms have already noticed copycat hackers using it.
The Mirai malware also appears to target products from other IoT vendors that use weak default passwords in their devices. Security experts have noticed the malware tries a list of more than 60 combinations of user names and passwords.
Last month, a Mirai-powered botnet also briefly took down the website of cybersecurity reporter Brian Krebs, by delivering 665 Gbps of traffic, making it one of the largest recorded DDOS attacks in history.
Daily “Answers” emails are provided for Daily News Articles, Tuesday’s World Events and Friday’s News Quiz.



